user_email) directly into integrations. The AI Agent never generates or modifies these values – they come from trusted sources only.
Configure actions with verified parameters so integrations receive trusted identities. The external system can then validate permissions (e.g., that a user can refund their own order). This prevents impersonation and unauthorized access.
Configure verified variables
Define verified variables in Guardrails (Settings → Guardrails → Verified Parameters tab).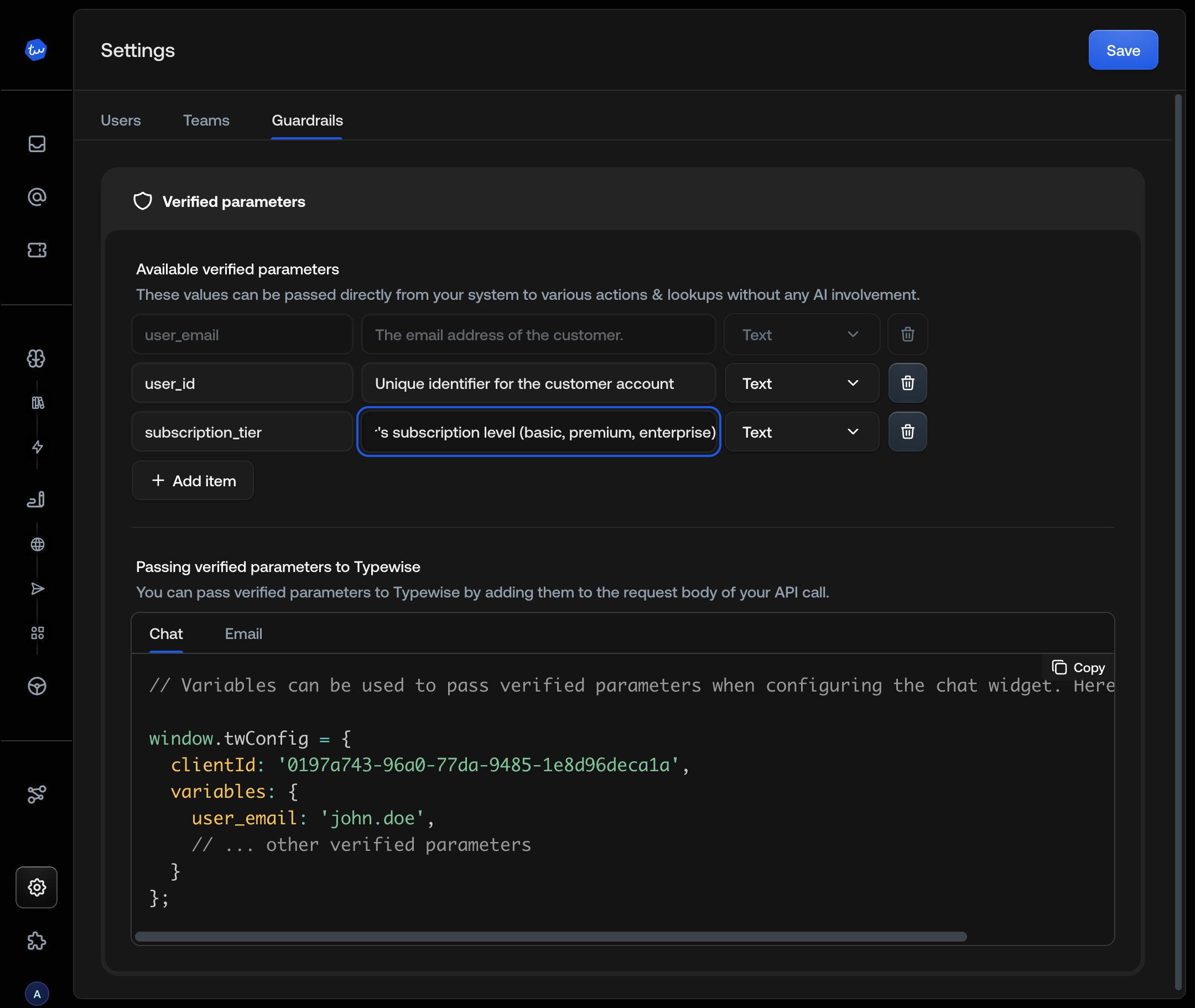
| Field | Description |
|---|---|
| Variable name | Key used in the payload (e.g., user_email, user_id) |
| Type | Text, Number, or Yes/No |
| Action | Delete or edit the variable |
The
user_email variable comes pre-configured and can’t be deleted. It’s always available for email verification.Verification by channel
Chat widget
Pass verified parameters through the chat widget configuration. Signed parameters are trusted.- The AI Agent asks the customer to reply
- Once they reply, Typewise verifies the email
- If verification fails, conversation hands off to a human agent
Typewise may request verification if the customer has only sent a single email without prior history.
Guardrails
Missing verified variable: If an action requires a variable that isn’t available, the system hands off to a human agent. Permission validation: The integration must check permissions. For sensitive actions like “Refund Order”, your MCP server or API must verify the user’s identity and authorization. See Guardrails settings to configure.Map parameters to actions
When configuring an AI action, map verified parameters to inputs:- Verified Parameter – from trusted context (e.g.,
user_emailfrom chat widget) - Static Value – fixed value for every execution
See also
- AI actions – configure automated actions
- Manual actions – human-executed actions
- Integrations – connect third-party services